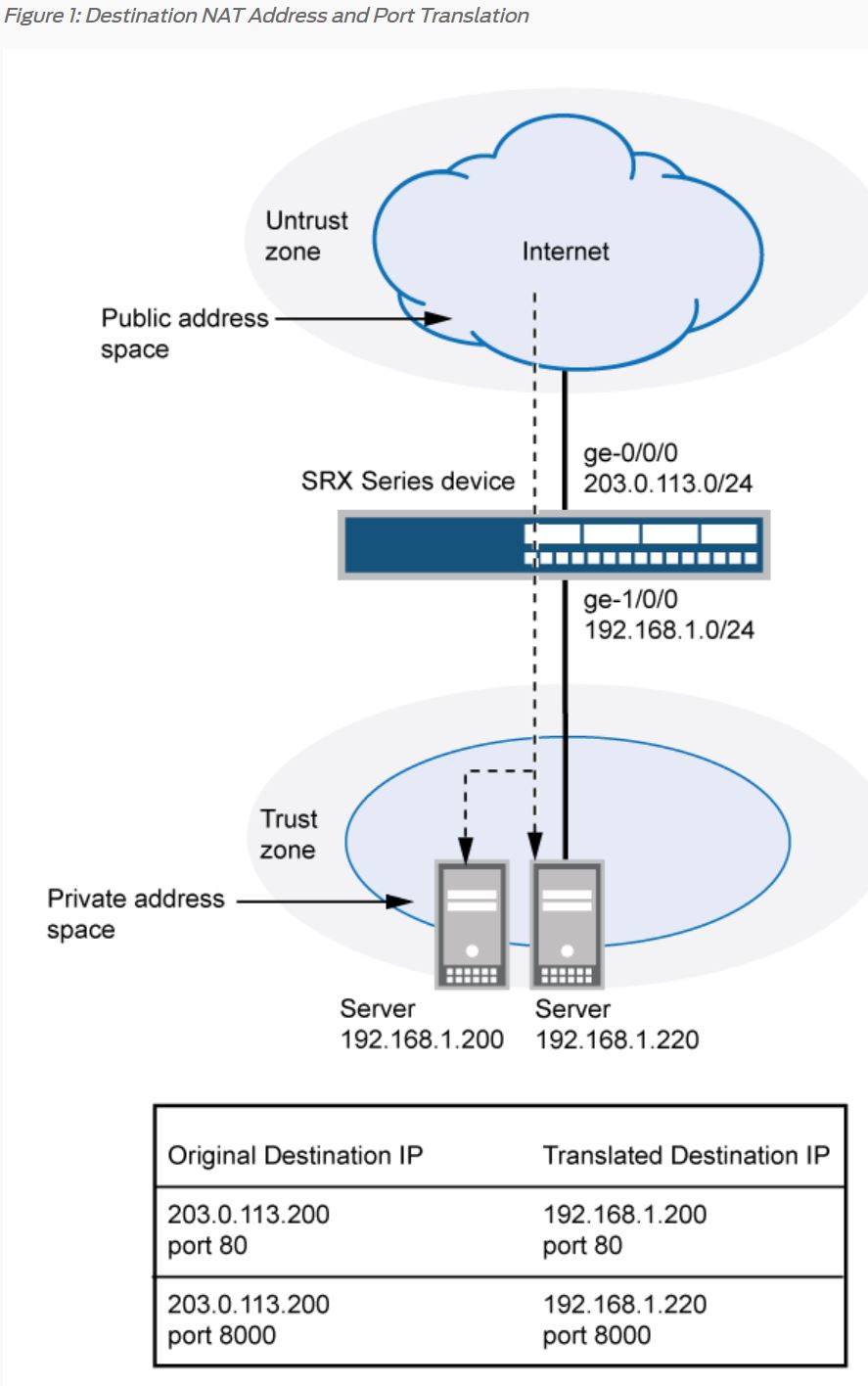
Example: Configuring Destination NAT for IP Address and Port Translation
Step-by-Step Procedure
The following example requires you to navigate throughout various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode.
To configure a destination NAT mapping from a public address to a private address:
- Create destination NAT pools.
[edit security nat destination]user@host# set pool dst-nat-pool-1 address 192.168.1.200 port 80user@host# set pool dst-nat-pool-2 address 192.168.1.220 port 8000
- Create a destination NAT rule set.
[edit security nat destination]user@host# set rule-set rs1 from zone untrust
- Configure a rule that matches packets and translates the destination address to the address in the pool.
[edit security nat destination]user@host# set rule-set rs1 rule r1 match destination-address 1.1.1.200user@host# set rule-set rs1 rule r1 match destination-port 80user@host# set rule-set rs1 rule r1 then destination-nat pool dst-nat-pool-1
- Configure a rule that matches packets and translates the destination address to the address in the pool.
[edit security nat destination]user@host# set rule-set rs1 rule r2 match destination-address 1.1.1.200user@host# set rule-set rs1 rule r2 match destination-port 8000user@host# set rule-set rs1 rule r2 then destination-nat pool dst-nat-pool-2
- Configure proxy ARP.
[edit security nat]user@host# set proxy-arp interface ge-0/0/0.0 address 1.1.1.200/32
- Configure addresses in the global address book.
[edit security address-book global]user@host# set address server-2 192.168.1.220/32user@host# set address server-1 192.168.1.200/32
- Configure a security policy that allows traffic from the untrust zone to the servers in the trust zone.
[edit security policies from-zone untrust to-zone trust]user@host# set policy server-access match source-address any destination-address [server-1 server-2] application anyuser@host# set policy server-access then permit





