Routing and Switching
IPV6
Types of IPv6 addresses There are few types of addresses w need to know about. These are: Global Addresses – Unique, global addresses used on the Internet. They use the following prefix 2000::/3 ( Routable ) Link Local Addresses…
Read more
Virtual Routing and Forwarding ” VRF “
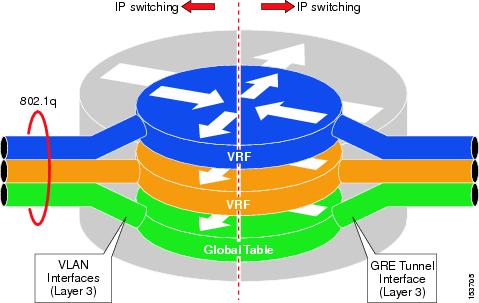
This is a quick remember for me, i will redo this section in more details soon. VRF “VPN Routing and Forwarding” VRF is used to isolate different clients, sites, etc… each vrf have its own routing table. Without MPLS it is…
Read more
LLDP “Link Local Discovery Protocol”
The Link Layer Discovery Protocol (LLDP) is a vendor-neutral link layer protocol in the Internet Protocol Suite used by network devices for advertising their identity, capabilities, and neighbors The protocol is formally referred to by the IEEE as Station and…
Read more
CDP “Cisco Discovery Protocols” Explain
CDP stand for Cisco Discovery Protocol and is a Cisco Proprietary Protocol and Interfaces must support SNAP ( Support Subnetwork Access Protocol ) Headers The standard industry equivalent is LLDP. CDP isn’t just a simple protocol there is more…
Read more
MPLS

Label Stack Fields Label = 20 bits EXP = 3 bits map the standard IP packet ToS into the Experimental field for MPLS CoS S = Stack bit is use to identify the end of the last label of the…
Read more
OSPF FILTERING
OSPF Filtering Using Distribute List with Prefix-List ! ip prefix-list BLOCK_L0 deny x.x.x.x/xx ip prefix-list BLOCK_L0 permit x.x.x.x/x ! router ospf 1 distribute-list prefix BLOCK_L0 in or out ! OSPF Filtering Using Distribute List with ACL ! ip access-list standard…
Read more
Cisco IOS Devices Best Practices
This checklist is a collection of all the hardening steps that are presented in this guide. Administrators can use it as a reminder of all the hardening features used and considered for a Cisco IOS device, even if a feature…
Read more
Diffie-hellman Explain Wouah !
Diffie-hellman Modulo Given two numbers, a (the dividend) and n (the divisor), a modulo n (abbreviated as a mod n) is the remainder from the division of a by n. For instance, the expression “7 mod 5” would evaluate…
Read more
How IPSec Works
To make it simple as for the configuration you need 5 things : Crypto Policy Transform-set Access-list Defining your crypto map Applying it to the interface Example of configuration : Key Components of creating an IPSec tunnel in chronological order:…
Read more
